Explore more
SOC to gain holistic security visibility across
on-premises, cloud, and hybrid networks
Detects sophisticated attacks and manages incidents effectively, remediating detected threats through its intuitive, advanced security analytics and monitoring capabilities.
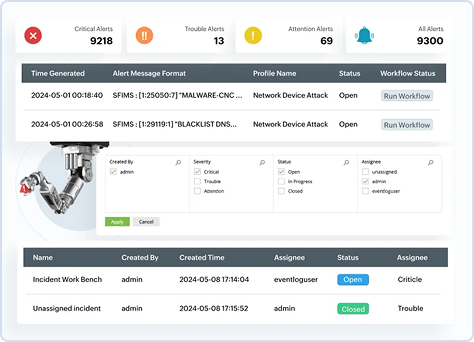
From alerts to actions: Automated TDIR
Vigil IQ, the automated TDIR (threat detection, investigation, and response) module, empowers your SOC to proactively combat threats, boost efficiency, and strengthen security posture.
Key Benefits
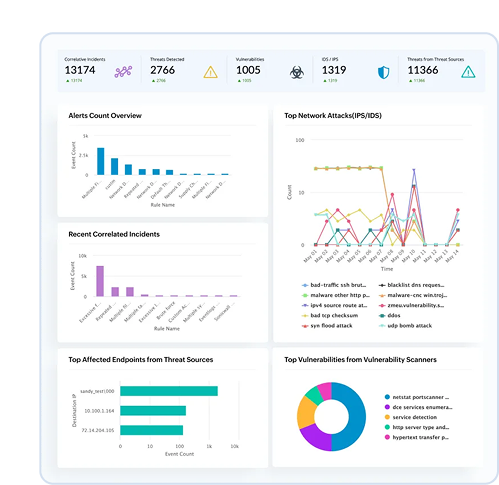
Enhanced Threat Detection: Multi-layered detection using real-time correlation, AI-driven anomaly detection, and signature-based analysis for faster, more accurate threat identification.
Faster Investigations: Centralized Incident Workbench aggregates critical telemetry for contextual analysis, with visual process lineage and AI-generated user and incident timelines.
Automated Response: Pre-built playbooks streamline threat response, enabling rapid action and minimizing impact.




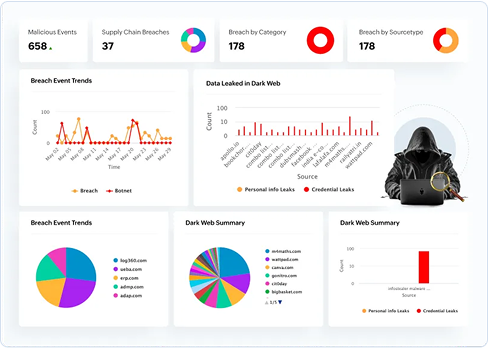
Proactive security adoption with dark web monitoring
Prevent data breaches from external threats with proactive dark web monitoring. Identify exposed credentials and personal data on the dark web, and gain actionable insights into breaches and supply chain leaks—before attackers can take advantage—keeping your enterprise one step ahead.
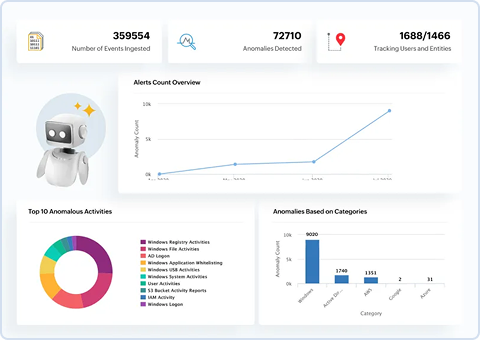
Tackle insider threats with AI-driven behavioral analytics
Detect potential user-based threats with AI-powered behavior analytics that continuously adapts to and analyzes user activity. Integrated UEBA with risk management helps prioritize suspicious behavior, uncovering both stealthy threats and complex attack patterns. User identity mapping and dynamic peer grouping enhance anomaly detection with rich user context.
Key Benefits
Enhanced Threat Detection: Multi-layered detection using real-time correlation, AI-driven anomaly detection, and signature-based analysis for faster, more accurate threat identification.
Faster Investigations: Centralized Incident Workbench aggregates critical telemetry for contextual analysis, with visual process lineage and AI-generated user and incident timelines.
Automated Response: Pre-built playbooks streamline threat response, enabling rapid action and minimizing impact.





Secure sensitive data from breaches
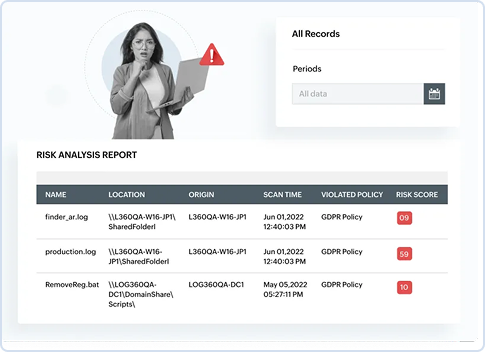
Identify sensitive data across your network with automated e-discovery and customizable policies tailored to locate specific confidential information. Classify data by risk level and type of personal information to enforce precise access controls. Integrity monitoring safeguards files on Windows systems and SQL databases from unauthorized changes, while AI-driven anomaly detection helps prevent data exfiltration.
Protect multi-cloud environment
with cloud security monitoring
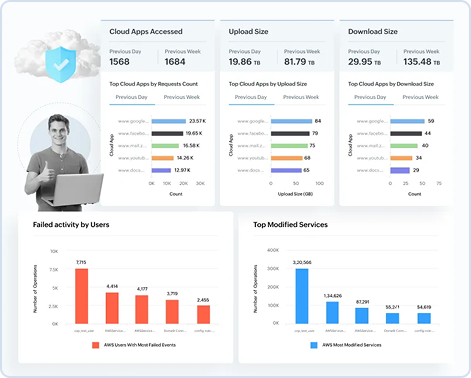
Gain visibility into security events across AWS, Azure, GCP, Salesforce, and more with comprehensive cloud security monitoring. Detect shadow IT, accelerate threat detection, investigation, and response, and ensure compliance with regulations using the built-in CASB module.
Key Benefits
Enhanced Threat Detection: Multi-layered detection using real-time correlation, AI-driven anomaly detection, and signature-based analysis for faster, more accurate threat identification.
Faster Investigations: Centralized Incident Workbench aggregates critical telemetry for contextual analysis, with visual process lineage and AI-generated user and incident timelines.
Automated Response: Pre-built playbooks streamline threat response, enabling rapid action and minimizing impact.





Security and risk posture management
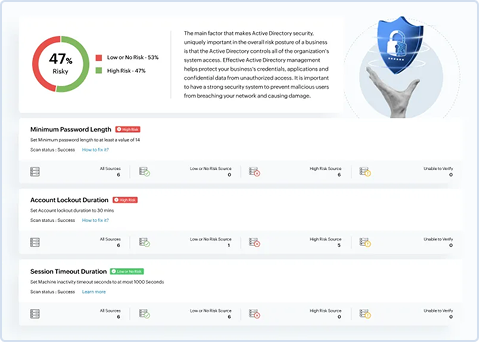
Get a complete view of security vulnerabilities in critical environments like Active Directory and MS SQL servers. The security and risk posture assessment uncovers misconfigurations and gaps, offering actionable insights into your network’s risk profile and attack surface. This enables you to prioritize and resolve issues before they turn into serious threats..
Security orchestration, automation, and response (SOAR)
Streamline security operations by automating routine tasks such as incident assignment, data enrichment, and investigation workflows, allowing analysts to focus on critical threats. SOAR lets you orchestrate complex workflows through pre-built playbooks for rapid threat mitigation and reduced impact. Its seamless integration with existing security tools enables coordinated responses, ensuring a unified defense against cyber threats.